1. Check your SSL settings
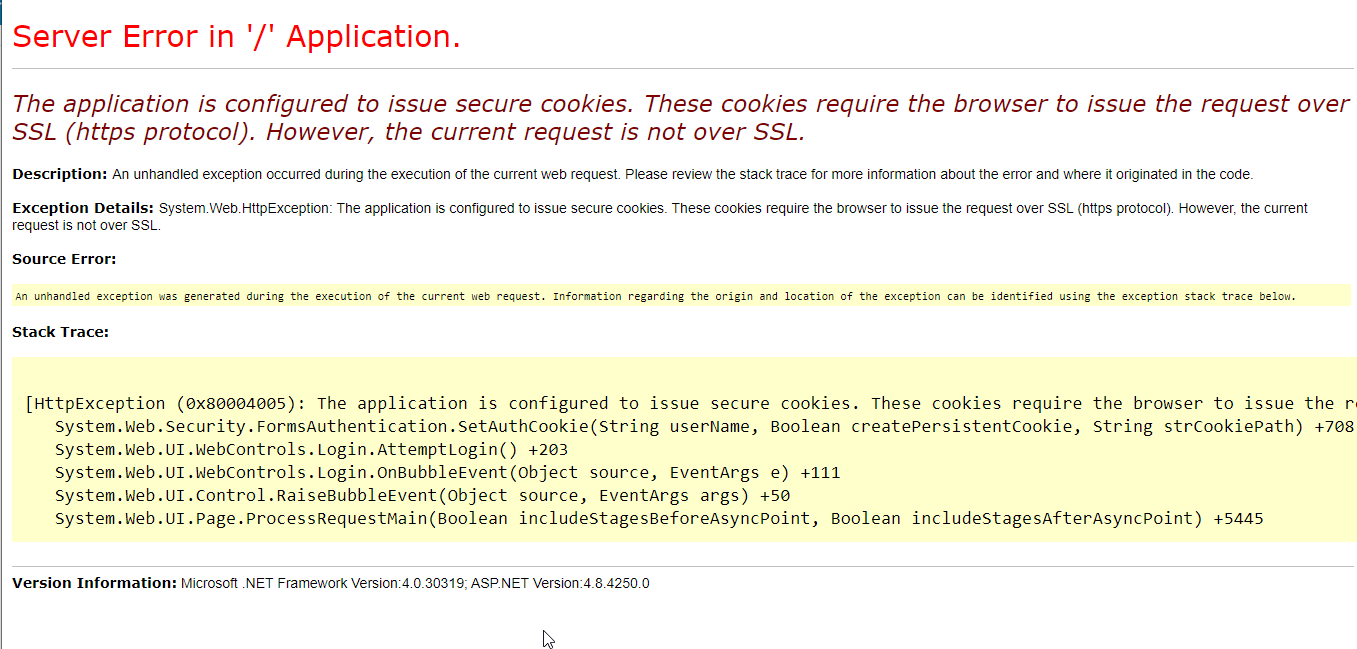
If this exception is happening in a local development environment, chances are you might be running your website over HTTP.
Whilst I would always recommend running a local site under HTTPs to mimic production as much as possible during local development, running it under HTTP could be one potential cause of this exception being thrown.
In your Web.Config, look for the authentication settings for the .EPiServerLogin form, and make sure requireSSL is set to false. Just make sure this never makes it to a public environment 🙂
<authentication mode="Forms"> <forms name=".EPiServerLogin" loginUrl="Util/login.aspx" timeout="120" defaultUrl="~/" requireSSL="true" /> </authentication>
2. Check your machine key
Another cause is a mismatch between the registered machine key in the database, and the machine key configured on the environment. For those running an on-premise web farm or utilising cloud hosting with multiple instances within the load, it’s important that the machine key is the same on each environment that has access to the Episerver database.
Simplest way to fix this is to configure it from the Web.Config. This will override any lower level machine key’s that may be configured in the machine.config on the local environment.
You should first generate a new machine key using one of the many tools out there, then a simple addition to the web.config on each environment will do the trick:
<configuration> <system.web> <machineKey decryption="AES" validation="SHA1" decryptionKey="Decryption key goes here" validationKey="Validation key goes here" /> </system.web> </configuration>
If all else fails.. switch off AntiForgery token validation
Note that this should never be done on an environment outside of your local network, as this is a feature that’s used specifically to prevent cross-site request forgery – which is a common security vulnerability in the modern web.
See how to switch it off here: https://www.c-sharpcorner.com/article/understand-antiforgeri-token-in-asp-net-mvc/